The following are the four general types of attacks:
- Interruption
- Interception
- Modification
- Fabrication
Interruption
A system asset is destroyed, made unavailable, or made useless. To put it another way, a network service is degraded or made unavailable for lawful purposes.
They are attacks against the availability of the network.
Examples of Interruption Attacks:
- Overburdening a server host to the point that it is unable to reply.
- Severing a chain of communication
- Overloading an intermediary network or network device to prevent access to a service.
- Requests are being redirected to invalid locations.
- There is a risk of software or hardware theft or destruction.
- File management systems are disabled.
Mitigate the attack:
- Firewalls can be used to allow or reject protocols, ports, or IP addresses. Modern stateful firewalls, such as the Check Point FW1 NGX and Cisco PIX, have the capacity to distinguish between legitimate traffic and DoS attack traffic.
- Maintaining appropriate backups of system configuration data.
- Replication.
Interception
An asset is accessed by an unauthorized person. A human, software, or a computer might be an unauthorized party. To put it another way, an unauthorized person obtains access to confidential or private data.
They are the attacks against the confidentiality objective of the CIA Triad.
Examples of Interception Attacks:
- Eavesdropping in on conversations.
- Telecommunications networks are being wiretapped.
- Copying files or programs without permission.
- Obtaining copies of messages in order to replay them later.
- To capture data from a computer system or network, packet-sniffing and keylogging are used.
Mitigate the attack:
- Encrypting the flow of information from source to destination – SSL, VPN, 3DES, and BPI+ are used to encrypt the flow of information from source to destination so that if someone is able to eavesdrop on the traffic, all they will see is ciphered text.
- Traffic Padding is a function that generates ciphertext output endlessly, even when plain text is not available. A random data stream is created endlessly. The plaintext is encrypted and sent when it is available. When there is no plaintext in the input, the random data is encrypted and delivered. As a result, an attacker will be unable to discriminate between tree data flow and noise, and hence will be unable to estimate the quantity of traffic.
Modification
An unauthorized person not only obtains access to an asset but also tampers with it.
This is an attack against the integrity of the information.
Basically, there are three types of modifications:
- Change: Make a change to the information that already exists. The information was previously available, but it was wrong. Change attacks can be used to target either sensitive or public information.
- Insertion: When an insertion attack is carried out, data that did not exist earlier is inserted. This attack might be used against historical data or data that hasn’t been acted on yet.
- Deletion: Deletion is the process of removing data from a system.
Examples of Modification Attacks:
- Modifying the contents of network communications.
- Changing data files and their contents.
- Changing programs to make them function better.
- System hardware or network topologies are being reconfigured.
Mitigate the attack:
- Intrusion detection systems (IDS) were introduced, which could check for various signatures that indicate an attack.
- Encryption methods are used.
- Padding for traffic
- Backing up your data
- Use checksums, sequence numbers, digests, and authentication codes as communications methods.
Fabrication
Counterfeit items are inserted into the system by an unauthorized entity. Simply said, a person introduces false information, resources, or services into a network.
This is an attack against authenticity.
Examples of Fabrication Attack:
- Using the identity of another person to send communications across the network.
- Replaying communications that were previously intercepted.
- The act of impersonating a website or other network service.
- Taking another host’s or service’s address and effectively-becoming that host or service.
Mitigate the attack:
- Authentication and authorization methods are used.
- Putting Firewalls to Work
- Use Digital Signatures – A digital signature method is a mathematical scheme for proving a digital message or document’s authenticity.







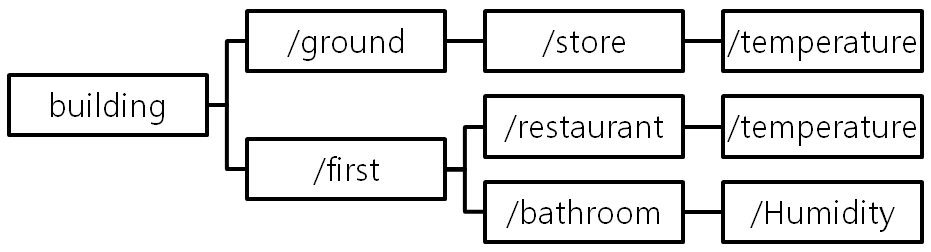
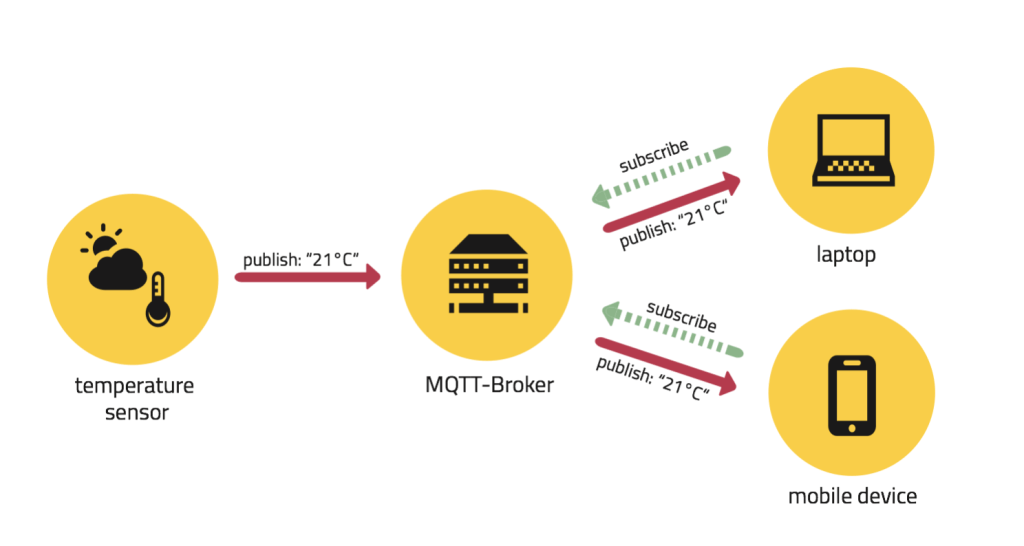

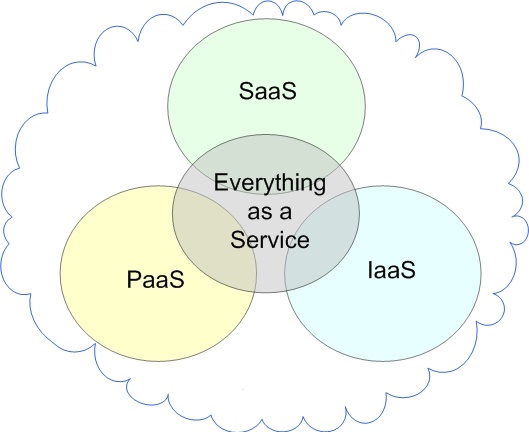
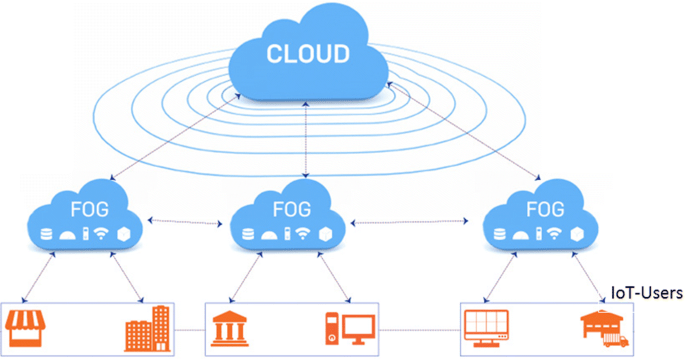



You must be logged in to post a comment.