In a bid to contain the spike in COVID-19 cases, the UK went on lockdown in November 2020. But despite having the same lockdown measures, infections in Kent were still rising. Due to an overall drop in the number of cases, the country eventually relaxed its lockdown restrictions. What happened next was nothing short of a nightmare. The number of cases skyrocketed. Researchers realized somewhere in Kent the virus had mutated. It was a new variant, and it was more contagious and was spreading extremely fast. In the next five months, this became the most common form of the virus.
But let us back up for a bit. Why did the COVID-19 virus mutate? Why do any virus mutate at all?
From an evolutionary standpoint, mutations are necessary accessories to natural selection. Most mutations are not beneficial for the organisms. Many mutations cause organisms to leave fewer descendants over time, but once in a while, there are changes that give the virus an advantage. These advantageous mutations led to the emergence of what are now called the Variants of concern.
Viruses are basically just a shell of protein surrounding some genetic material- either DNA or RNA. That genetic material is made up of molecules that can be represented by a series of letters like this

Each part of the genetic code contains instructions for how to make one specific protein that allows the virus to function. The virus has one goal- to make more copies of itself. But because they are extremely simple entities they use us to replicate. Whenever a virus infects someone, it takes over their cells to make more and more copies of themselves. This means tediously replicating the same code repeatedly. Occasionally, however, the virus makes a mistake. This is called a mutation, and it slightly changes the instructions for making the virus. This altered virus is a variant.
Coronaviruses have a specific type of proteins called the spike proteins that they use to bind with and infect the human cell. Luckily for us, this binding is not a perfect fit and the virus cannot always get past the cell’s defenses. What happened with the UK variant or the B.1.1.7 variant is that it had a mutation on the spike itself making the binding better.
The deadly second wave of Coronavirus that wreaked havoc globally, had a cataclysmic effect in India. WHO recently announced that the highly infectious virus variant which was first detected in India will be referred to as the ‘Delta variant.’ As per data, the Delta variant or the B1.617.2 was the primary cause behind India’s devastating second wave and is much more infectious than the Alpha strain (B.1.1.7), which found in the UK.
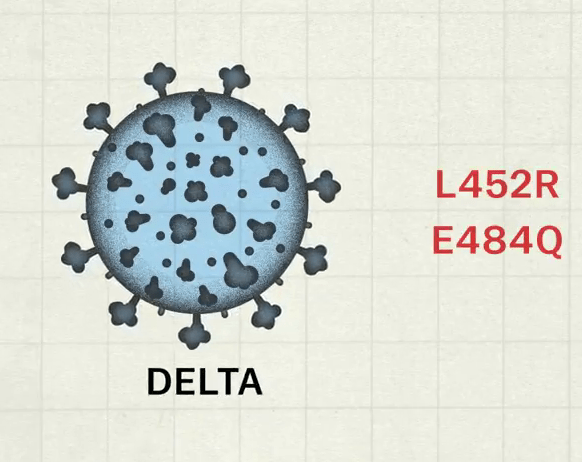
The Delta variant has many different mutations, two of which had been seen earlier. These mutations seem to make the virus more transmissible and confers it power to re-infect people. This means the Delta variant evolved as a response to our immune system.
The Delta plus variant, a new mutant version of the Delta strain first detected in India, has been found in 22 cases in Maharashtra, Kerala and Madhya Pradesh and is a “variant of concern”, the government said in a warning to these states this evening. Sharing preliminary details of the Delta-plus variant, researchers at CSIR-Institute of Genomics and Integrative Biology (IGIB) said that it may be linked with abilities to better escape immune response, which means the virus can potentially dodge vaccines and antibody therapies. In fact, Vinod Scaria, a scientist with IGIB, said that there is also evidence of the Delta-plus variant’s “resistance to monoclonal antibodies”, putting into question the effectivity of the monoclonal antibody cocktail that was recently okayed for the treatment of milder cases.
The tsunami we witnessed in the second wave of the pandemic, caused by the delta variant, has only started to ebb. The rise of a new mutant, merely months after the initial detection, makes the Delta plus variant a serious cause of concern, at least on paper.






You must be logged in to post a comment.