The presence of the doctor is the beginning of the core.Doctor’s day is celebrated on 1st july .It is an occasion to marked to pay tribute to the doctor and their contribution in the society .In india,it is celebrated in honour Dr. Bidhan Chandra Roy’s birth and death anniversary .
Category: Science
Types of Security Attacks
Active Attacks
It is an attempts to alter system resources or affect their operation. It includes Modification of data, or creation of false data.
Four categories
Masquerade
Replay
Modification of messages
Denial of service
- Masquerade : It takes place when one entity pretends to be a different entity. For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus enabling an authorized entity with few privileges to obtain extra privileges by impersonating an entity that has those privileges.
- Replay : Replay involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect.
- Modification of Messages : Modification of messages simply means that some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect.
- Denial of Service : The denial of service prevents or inhibits the normal use or management of communications facilities. This attack may have a specific target; for example, an entity may suppress all messages directed to a particular destination (e.g., the security audit service). Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance.
Passive Attacks
It attempts to learn or make use of information from the system but does not affect system resources. Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted.
Two types of passive attacks:
- Release of Message Contents
- Traffic Analysis
- Release of Message Contents : A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions.
- Traffic Analysis : The opponent could determine the location and identity of communicating hosts and could observe the frequency and length of messages being exchanged. This information might be useful in guessing the nature of the communication that was taking place.
Computers in detail
Definition
A computer is a machine that performs tasks and calculations according to a series of instructions or program operations (circuits, etc.) and software (OS, the underlying software that controls the hardware when the user issues instructions).

Programming
You don’t need a car, its function is the same as a jukebox that keeps playing tracks. For example, they want to tell the music box to play different music every time. They want to program the music box so that it can play different music. This part of the history of computers is called “the history of programmable machines.” “This is a concise sentence in the history of machines. When I speak their language, I can order to do different things.”
The role of computers in daily life
Today’s computers are fast, small and small. Powerful. Computers can save money, time and labor; otherwise it would take months or years to complete in a few seconds with computers. Launch satellites using a simple application on our desktop. According to the requirements, the storage capacity and speed of the computer will be different. For example, NASA and other companies that use high-speed supercomputers, because speed is an important part of your business. Computers are cheaper than smart phones. The essence is in hand. At home, computers provide opportunities to access social networks, read books, or work from home.In the office, they are the most important because they are the most important form of work. Although computers can help with almost everything from shopping to work to taking notes or playing games, people rely heavily on computers for almost everything. Computers make life easier and faster than ever. Large storage rooms are of great help to today’s business. The data received from different systems is stored on the computer for later use. In addition, previous shopping, reading, work, arithmetic, calling appointments and events or activating alarms all occurred in different places. Now everything can be done with our smart phone. If the book is bulky, it would be great to bring ten books. Now; millions of books are within reach. There is no need to check calendars anymore, because they have been replaced by reminders that automatically remind us of important events and clocks that only need to be activated once. These are some basic tasks that are performed daily, and it is difficult to work without a computer. Computers are no longer a luxury, they can be used in different forms on different platforms, for example as smart phones. Computers are also very helpful in medicine and have undergone extensive development in the past decade. Addictive.All in all, we can say that computers have profoundly affected our lives, and changes are no longer associated with ease, habit, and popularity.
The above is a small example of computers, but as far as modern technology is concerned, computers have changed our way of life. Computers are not only used for arithmetic but are now active in teaching, industrial purposes, automated processes, data management, analysis, personal and group entertainment, Music synthesis, professional photo and video editing, hardcore games, research goals, creating new software and applications to make life easier, shopping, banking, marketing, and even participating in the artificial creation of intelligent creatures with deep learning concepts and machine learning.
Humans made the conditions for the pupfish’s extinction- now humans keep it alive.
The pupfish, also known as the rarest fish in the world, are a group of killifish with striking coloration. They are mostly found in the extreme and isolated environment. These rare species of fish lives in a single pool in the Mojave Desert. They went almost extinct with their only canyon pool being pumped.
The description of Pupfish
Pupfish are small, colorful, knuckle-sized and ray-finned fishes. The most famous amongst them are the Devil’s Hole pupfish. The Devil’s Hole pupfish are bright blue with purple accents whereas, the white sands pupfish has yellow and orange fins. Most of the pupfish are very tiny, some even less than an inch in length.
The diet of these pupfish includes variety of things, consisting of algae, plants, aquatic invertebrates and some insects.

About the devils hole pupfish
The fascinating and playful pupfish with bright, silvery-blue and lustrous body are found in an oasis within the Death Valley called as- The Devils Hole. These mighty goldfish-like fishes survive in the 92 degrees water of the Devil’s Hole. They withstand harsh conditions that would kill most other fish. Another fact about this fish is that it acts as an indicator of seismic activity around the globe.
Hottest, Driest and the Lowest National Park
The Death Valley as the name sounds is a land of the most extreme conditions. You can expect a scorching heat of 110 F to 120 F +. Even though this land experiences droughts and record summer heat, in the winters the peaks of the mountains are snow-laden. This land welcomes rainstorms rarely. Lush oases harbor tiny fishes and refuge for wildlife and humans. The name might sound very morbid but it is home to a great diversity of life.
What threatened their existence?
In the late 1960’s and early 1970’s, groundwater was pumped out extensively for the agricultural purposes. This activity led to a major downfall of the water level in Devil’s Hole. These invasions were a threat to the very existence of this fascinating species.
So, a group of academics, government employees and private citizens met in 1969 to speak about the protections needed for the fauna in Devil’s Hole.
The desert pupfish has been classified as endangered by IUCN. Due to the pumping of the aquifer since 1960’s, the fish never recovered. Later, it was decided that a back-up population was needed. A replica was created where one part of the population resides in the fake canyon, and the other in the natural canyon.
How many Devils Hole pupfish are left in 2020?
The observable population of the Devil’s Hole pupfish has reached 136. In the years 2006, 2007, and 2013 their population was less than 40. In the 1970s, 1980s, and 1990s, scientists counted near about 200 Devils Hole pupfish. And in the late 1990s there was startling decline in their numbers.
“Despite these extremes, Devils Hole pupfish continue to display their resiliency that have allowed them to survive for thousands of years”, said Brandon Senger, Supervising Fisheries Biologist for the Nevada Department of Wildlife (NDOW).
Network Security

Network security refers to the monitoring and control of illegal access, exploitation, and any undesired changes to the networking system. A computer networking system strategy that ensures the security of an organization’s assets, software, and hardware resources is known as network security.
Why Do We Need Network Security?
Connecting our gadgets to the internet and other networks offers us a whole new world of possibilities. We can get the information we need without keeping it on our gadgets indefinitely. We are able to interact with one another, which allows us to collaborate and coordinate our efforts. The networks that enable us to operate our lives are made up of these linked gadgets.
Unless properly secured, any network is vulnerable to malicious usage and accidental harm. Private data, such as trade secrets and client information, might be revealed due to hackers, disgruntled workers, or inadequate security measures inside the business.
For example, losing private research can cost a company millions of dollars by robbing it of the competitive advantages it paid for. While hackers steal consumer information and sell it to be utilised in fraud, the company suffers poor press and public confidence.
Rather than causing network damage, most frequent network assaults are aimed to obtain access to information through spying on users’ conversations and data.
Attackers, on the other hand, may do more than just take data. They may be able to cause harm to users’ devices or manipulate systems in order to obtain physical access to facilities. This puts the organization’s assets and members in jeopardy.
Data is kept safe, and susceptible systems are protected from outside tampering, thanks to effective network security measures. This helps network users to be secure while focusing on the organization’s objectives.
Information security is needed for the following given reasons:
- Unwanted Changes – To secure information against unauthorized users unintentionally or purposefully altering it.
- Information Loss and Proper Delivery – To prevent data loss and ensure that it reaches its rightful owner in a timely manner.
- Non-repudiation – To ensure that each node receives an acknowledgement of a message in order to defend against the sender’s rejection in particular scenarios. Let’s say a consumer places an order to buy a few shares of XYZ in the broader market, but the transaction is denied after two days since the rates have dropped.
- Hiding the Identity of the Original Sender – To prevent a certain network user from sending any mail or message in such a way that it seems to the recipient that it was sent by a third party. For example, a user X creates a message with some favourable instructions for his personal benefit and sends it to user Y in such a way that Y accepts the message as coming from Z, the organization’s boss.
- Inappropriate Delay – To protect the data from any unintentional delays in the path taken to deliver it to the intended destination within the specified time frame.
- Corrupting or Deleting – To protect our hardware, like as hard drives, PCs, and laptops, from malware, viruses, and other threats that might harm our system by corrupting or destroying all of the data contained on it.
- Malware & Unwanted Software – To safeguard our computers against malicious software that, if installed, can destroy our systems in the same way that hackers do.
The Hot Planet Story
Two frogs are playing in a pond, then suddenly, BAM! They are kidnapped and taken to a kitchen by a chef. The chef boils up a pot of water and throws one frog inside. Sensing danger, the frog jumps out of the pot and escapes. The chef tries a different strategy with the other frog. This time, he turns on the heat slowly so that the frog doesn’t realize that it is being cooked.
REST IN PEACE Froggy.
Are we not facing the same situation? Yes, Global Warming.

Global warming is the increase in the average temperature of the earth. It is one of the greatest environmental challenges.
Global warming is caused due to many reasons, the primary one being human activity. Greenhouse effect is the main cause of global warming. A greenhouse is made of glass which helps the plants stay warm even when it is cold outside. Similarly, the greenhouse gases like methane and carbon dioxide act as an insulation to keep us warm. This is a natural process. But if more and more greenhouse gases enter the atmosphere, the earth becomes warmer rapidly. But what causes this?
Here we go again….. Human activity.
Over population
Deforestation
Burning of fossil fuels
Industrialization
All this leads to melting of glaciers which increases the sea level. This further leads to change in ecosystem. Rise in droughts, forest fires, hurricanes, and desertification are also caused due to global warming
Still, global warming remains to be a controversy, leading to many debates. Some people believe that global warming is just a natural cycle and the drastic climate changes have nothing to do with human activity. In my opinion, blaming the nature is not right. Since we are greedy and don’t want to fix the issue, we find such excuses.
Now moving on the solutions.
- Spreading awareness, is a great step to fight against global warming, that is what this article is about, isn’t it?
- Simple solutions like unplugging devices when not in use, carpooling, using LED lights and CFLs, planting trees and recycling can both save money and reduce our carbon footprint.
- Using renewable energy sources, zero-carbon technologies like wind turbines, solar panels, and biomass boilers can be built to conserve energy.
- Start-ups that develop such technologies should be encouraged and offered tax and loan incentives.
We can take such measures to protect our planet. Together we shall fight climate change and protect our dearest planet.

INDIA AND INDUSTRIAL REVOLUTION 4.0 Part-2

This article is in continuation with the previous part INDIA AND INDUSTRIAL REVOLUTION 4.0 Part-1.
Reasons why Industrial Revolution 4.0 is lagging-
1. Security is a crucial foundation of the Internet while the major challenge for the Industrial Revolution 4.0. As time goes the trend of Industrial Revolution 4.0 inflates from millions of devices to billions. As increasing the number of connected devices, the chance to exploit safety vulnerabilities is also increasing, in cheap or low standard designed devices, due to incomplete data streams, the chances of data theft is increased by which people’s health and safety can be risky. Many IoT arrangements will also include collections of similar or adjacent similar devices. This homogeneity expands the potential impact of any single security weakness by the total number of devices that all have the same features.
2. As Authenticity, trustworthiness and confidentiality are important aspects there are some other requirements also important like discriminatory access to certain facilities, preclude them from sharing with other things at certain Times and business communications involving smart objects would need to be secure from opponents’.The data networks are still delicate and also costly in comparison to other developed countries. From an Indian perspective, the cloud storage operation is still in the emerging stage. Transmit the data to a cloud service for processing, sometimes includes a third party. The gathering of this information leaks legal and regulatory challenges facing data protection and privacy law. To realize the opportunities of the Industrial Revolution 4.0, some new strategies will be required for privacy choices through a broad range of expectations, while still developing innovation in new technologies and services.
3. Absence of standards and documents can assist Senseless activities by devices. Low standard or cheap designed and configured devices have undesirable consequences for the networking resources. Without standards to guide developers and manufacturers, sometimes design products that operate in disruptive ways on the Internet. When any technology has a standard development process then it can be easily available everywhere and can be used by all applicants and increase the growth also. While in today’s world, global standards are followed by every local station.
4. Implementation of every technology requires a team of skilled persons who have ample knowledge of network, hardware, software and about that technology. And India is developing at this point where manpower thinks when technology is spread, they lose their job and there is no life of new technology. So, they don’t take any initiative to learn about it. So, every organization face lots of problem during their changeover phase from the legacy systems to IoT enabled systems. Similarly, Scalability, Fault tolerance and Power supply are also big challenges in India.
5. Advanced technologies require advanced mechanisms which require more amount of money. As India is a developing country, it is not possible to invest on a large scale in Industrial Revolution 4.0. As a result of failed fueled ‘money’, India is not able to cope with Industrial Revolution 4.0.
6. Another major problem with a developing country like India is the fuel needed to run. While the population is on a way steady rise, demand is quite increasing. India produced 557 million tons (metric tons) of coal in 2012-13, and India’s rapidly growing power industry consumed the majority of it. Coal production has steadily increased since the industry was nationalized in the 1970s. A trend almost certain to accelerate as the country faces growing urbanization and an expanding middle class, India has a high dependence on imports for its petroleum needs and is the world’s fourth-largest importer of crude oil.
7. The percentage of illiteracy in India is alarming. Every five persons among ten in India are illiterate. The condition in villages is worse than in cities. Though several primary schools have been set up in rural India, the problem persists. Also, providing education just to children won’t solve the problem of illiteracy, as many adults in India are also untouched by education. The education system of India is blamed now and then for being too theoretical but not practical and skill based. Students study to score marks, not to gain knowledge. This so-called modern education system was introduced by the colonial masters to create servants who could serve but not lead, and we still have the same education system. Rabindranath Tagore had written many articles offering suggestions to change the education system of India. But still, success is as elusive as ever.
Read more about India and Industrial Revolution in next part, INDIA AND INDUSTRIAL REVOLUTION 4.0 Part-3.
THE DOUBLE SLIT EXPERIMENT
One of the most famous experiments in physics is the double slit experiment. It demonstrates, with unparalleled strangeness, that little particles of matter have something of a wave about them, and suggests that the very act of observing a particle has a dramatic effect on its behaviour.
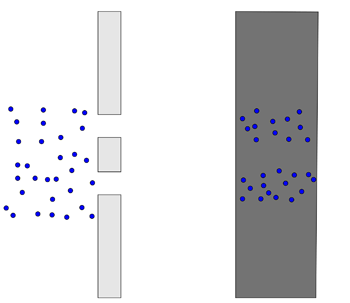
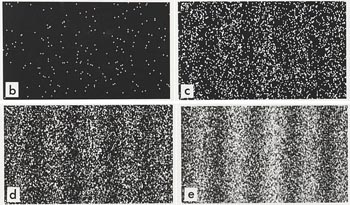
To start off, imagine a wall with two slits in it. Imagine throwing tennis balls at the wall. Some will bounce off the wall, but some will travel through the slits. If there’s another wall behind the first, the tennis balls that have travelled through the slits will hit it. If you mark all the spots where a ball has hit the second wall, what do you expect to see? That’s right. Two strips of marks roughly the same shape as the slits.
In the image below, the first wall is shown from the top, and the second wall is shown from the front.
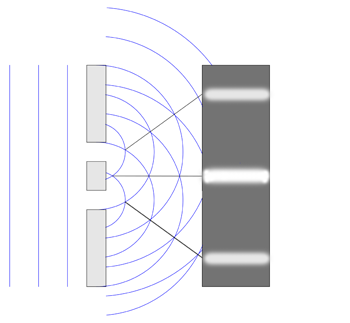
Now imagine shining a light (of a single colour, that is, of a single wavelength) at a wall with two slits (where the distance between the slits is roughly the same as the light’s wavelength). In the image below, we show the light wave and the wall from the top. The blue lines represent the peaks of the wave. As the wave passes though both slits, it essentially splits into two new waves, each spreading out from one of the slits. These two waves then interfere with each other. At some points, where a peak meets a trough, they will cancel each other out. And at others, where peak meets peak (that’s where the blue curves cross in the diagram), they will reinforce each other. Places where the waves reinforce each other give the brightest light. When the light meets a second wall placed behind the first, you will see a stripy pattern, called an interference pattern. The bright stripes come from the waves reinforcing each other.
Here is a picture of a real interference pattern. There are more stripes because the picture captures more detail than our diagram.
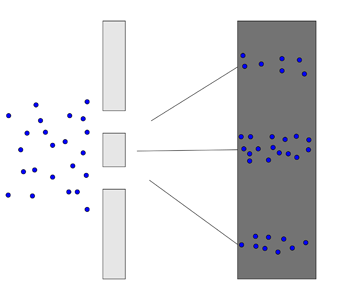
Now let’s go into the quantum realm. Imagine firing electrons at our wall with the two slits, but block one of those slits off for the moment. You’ll find that some of the electrons will pass through the open slit and strike the second wall just as tennis balls would: the spots they arrive at form a strip roughly the same shape as the slit.
Now open the second slit. You’d expect two rectangular strips on the second wall, as with the tennis balls, but what you actually see is very different: the spots where electrons hit build up to replicate the interference pattern from a wave.
Here is an image of a real double slit experiment with electrons. The individual pictures show the pattern you get on the second wall as more and more electrons are fired. The result is a stripy interference pattern.
What does the experiment tell us? It suggests that what we call “particles”, such as electrons, somehow combine characteristics of particles and characteristics of waves. That’s the famous wave particle duality of quantum mechanics.
Planetoids : Asteroids

An asteroid is a minor planet of the inner Solar System. Historically, these terms have been applied to any astronomical object orbiting the Sun that did not resolve into a disc in a telescope and was not observed to have characteristics of an active comet such as a tail.
As minor planets in the outer Solar System were discovered that were found to have volatile- rich surfaces similar to comets, these came to be distinguished from the objects found in the main asteroid belt.
The term “asteroid” refers to the minor planets of the inner Solar System, including those co- orbital with Jupiter. Larger asteroids are often called “Planetoids”.
Asteroids vary greatly in size from almost 1000km for the largest down to rocks just 1 meter across. The three largest are very much like miniature planets : they are roughly spherical, have at least partly differentiated interiors, and are thought to be surviving protoplanets.
“This planet is 15 million years overdue for an asteroid strike like the one that killed the dinosaurs.” – L Niel Smith
“If the Earth gets hit by an asteroid, it’s game over. It’s control-alt-delete for civilization.” – Bill Nye
The vast majority, however, are much smaller and irregularly shaped; they are thought to be either planetesimals or fragments of larger bodies.
The four largest asteroid-
- Ceres – 939km
- Vesta – 525km
- Pallas – 512km
- Hygiea – 434km

International Asteroid Day
Asteroid Day is an annual global event which is held on the anniversary of the Siberian Tunguska event that took place on June 30, 1908, the most harmful known asteroid- related event on Earth in recent history.
Asteroid Day aims to raise awareness about asteroids and what can be done to protect the Earth, it’s families, communities and future generations.
“The idea is to raise awareness of, not only the dangers of asteroids but also the fact that we have solutions in hand to find dangerous asteroids and do something about it.” – Tom Jones
“Sooner or later disasters such as an asteroid collision or a nuclear war could wipe us all out, but once we spread out into space and establish independent colonies, our future should be safe”. – Stephen Hawking
https://www.jagranjosh.com/general-knowledge/world-asteroid-day-quotes-1593472957-1
https://www.azquotes.com/quotes/topics/asteroids.html
Why Polar Bears are on The Verge of Extinction

The loss sea ice habitat from climate change is the biggest threat to the survival pf polar bears. Other reasons include human-polar bear conflict, toxic pollution, oil spills and potential hunting of some subpopulations.
Polar Bear-Human Conflicts
As the sea ice of the Arctic thins and disperses, increasing number of polar bears spend longer periods in along the Arctic coastlines. Here their powerful sense of smell attracts them to human communities. Scent leading to garbage, stored food, dog teams, and animal carcasses bring them into greater conflict with people residing in the Arctic.
As apex predators, polar bears pose a significant threat to human life and property. In recent years the attacks on humans, who come within the polar bear’s range, continue to rise.
Effects of Climate Change

Due to climate change the Arctic is heating up twice as fast as anywhere in the world, melting the sea ice cover by 14% per decade. Comparing the data recorded between 1981-2010, we have lost about 770,000 square miles.
Polar bears rely on sea ice as their hunting ground and to rest, breed, and store energy for the summer and sutumn, when food can be scarce. The bears health decline as they go longer periods without food. Bears that come ashore, after the ice breaks up, are roughly 22 pounds lighter and in poorer condition. They also must travel long distances to stay with the rapidly receding ice.
Polar bears suffering from malnutrition can face extreme starvation -especially females with cubs. Scientists have found the main cause of death for cubs to be either lack of food or lack of fat on nursing mothers.
Industrial Impacts

As summer ice retreats, a new ocean is emerging, which allows more opportunities for industrial development at sea, and on large parcels of land. Offshore petroleum installations and operations in the Arctic are expected to increase in number. This results in destruction of habitat, poisoning of the bears when they ingest oil and contaminated prey which causes disturbance in the food web. As traffic by oil tankers and cargo ships in Arctic waters increases, so do the oil spills and human disturbance to their habitat.
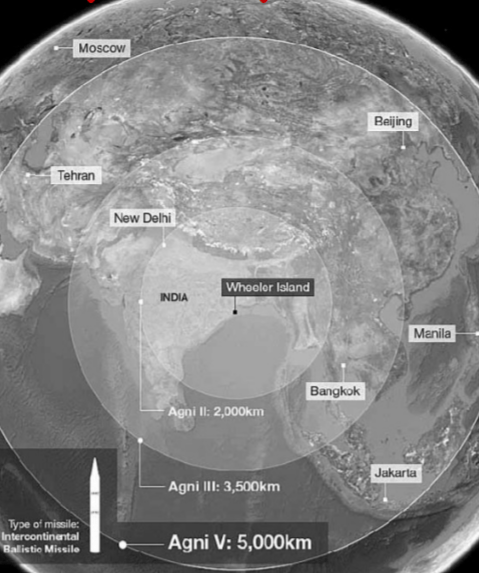
AGNI CLASS OF MISSILES
• Agni-1, Agni-2, Agni-3, Agni-4, Agni-5 and Agni-P.
• Designed & developed by DRDO.
• Family of medium to intercontinental range
ballistic missiles.
• can be fired from road- and rail-mobile launchers.
• powered by solid propellants.
• Agni-1 to Agni-5 – product of the Integrated Guided Missile Development Project (IGMDP).
• Inducted into Services to act as deterrence & meet the country’s security requirements – credible deterrence against China and Pakistan.
Agni-1
• medium-range ballistic missile – range of 700-800 km. • weight – 12 tonnes; length – 15 meters.
• capable of carrying a conventional payload of
1,000 kg or a nuclear warhead at a speed of
2.5 km/s.
• operational with the
Strategic Force Command
of Indian Army.

Agni-2
• surface-to-surface nuclear-
capable missile.
• Intermediate-Range Ballistic Missile (IRBM) – capable to cover the range of 2,000- 2,500 km.
• length is 20 meters, with the diameter of 1 meter.
• weight – 18 tonnes.
• 2 stages – solid propellant in
both of its stages.

Agni-3
• It is an IRBM – range of 2500-3,000 km.
• powerful solid propellant in its both stages.
• can carry a warhead of 1.5 tonnes.
• claimed that the missile’s circular error probable
(CEP) lies within of 40
meters – most accurate
and deadliest strategic
ballistic missiles of range
class in the world.

Agni-4
• range of 3500-4000km.
• earlier termed as Agni II
prime
• can carry a warhead of 1
tonne.
• two-stage missile.
• length is 20 meters and
launch weight is about 17
tonnes

Agni-5
• intercontinental surface-to-surface ballistic missile.
• India’s first ICBM.
• range – more than 5,000 km
• long-range
• Length – 17.5 m; weight – 50
tonnes.
• 3 propulsion stages.
• can carry a warhead weighing more than a tonne. • uses a canister launch missile system or Canisterisation of missile.
Canisterisation of missile
• warheads are pre-mated to the delivery vehicle and kept sealed for storage and transport.
• provides increased readiness – shorter
response time with an ability to launch in “just a few minutes”.
• provides necessary operational flexibility to
the forces.
• enhances missile longevity – protects the solid fuel from the elements.
Agni-P missiles
• successfully test-fired.
• new-generation advanced variant of Agni class of missiles – advanced
version of the ‘Agni-1’ missile.
• designed and developed by DRDO.
• will strengthen India’s credible deterrence capabilities.
• Features:
Nuclear-capable ballistic missile.
Canisterised missile.
range – between 1,000 and 2,000 kms.
surface to a surface missile that can
carry a payload of around 1,000 Kg or a nuclear warhead.
two-stage missile – composite rocket motors.
guidance systems equipped with electromechanical actuators.
solid-fuelled weapon system – state-of- the-art navigation system.
Can be fired from road and rail-mobile launchers.
complete technology upgrade in every way possible – improved parameters, manoeuvring and accuracy.
sleek missile that weighs less than its previous variant – due to the integration of new technologies.
Venus- Earth’s Twin
Venus is the second planet from the Sun. in our Solar System. It is the brightest natural object in Earth’s night sky after the Moon. Venus is one of the four terrestrial planets in the Solar System, meaning that it is a rocky body like Earth. It is similar to Earth in size and mass, and is often described as Earth’s “sister” or “twin”. The diameter of Venus is 12,103.6 km (7,520.8 mi)—only 638.4 km (396.7 mi) less than Earth’s—and its mass is 81.5% of Earth’s. Conditions on the Venusian surface differ radically from those on Earth because its dense atmosphere is 96.5% carbon dioxide, with most of the remaining 3.5% being nitrogen. The surface pressure is 9.3 megapascals and the surface temperature is 737 K (464 °C; 867 °F), above the critical points of both major constituents and making the surface atmosphere a supercritical fluid(distinct gaseous and liquid phases do not exist).
Some facts about Venus:
Diameter- 12,103.6 km
Orbital period- 224.7 days
Length of a day- 117 days
Axis tilt- 177.3 degrees
Distance from the Sun- 108 million km (0.72AU)
Moons- none
Atmosphere and climate
Venus has an extremely dense atmosphere composed of 96.5% carbon dioxide, 3.5% nitrogen—both exist as supercritical fluids at the planet’s surface—and traces of other gases including sulfur dioxide. The mass of its atmosphere is 92 times that of Earth’s, whereas the pressure at its surface is about 93 times that at Earth’s—a pressure equivalent to that at a depth of nearly 1 km (5⁄8 mi) under Earth’s oceans.
Studies have suggested that billions of years ago, Venus’ atmosphere could have been much more like the one surrounding the early Earth, and that there may have been substantial quantities of liquid water on the surface. After a period of 600 million to several billion years, solar forcing from rising luminosity of the Sun caused the evaporation of the original water. A runaway greenhouse effect was created once a critical level of greenhouse gases (including water) was added to its atmosphere. Although the surface conditions on Venus are no longer hospitable to any Earth-like life that may have formed before this event, there is speculation on the possibility that life exists in the upper cloud layers of Venus, 50 km (30 mi) up from the surface, where the temperature ranges between 303 and 353 K (30 and 80 °C; 86 and 176 °F) but the environment is acidic. The apparent detection of phosphine in Venus’ atmosphere, with no known pathway for abiotic production, led to speculation in September 2020 that there could be existing life currently present in the atmosphere.
Structure
The similarity in size and density between Venus and Earth suggests they share a similar internal structure: a core, mantle, and crust. Like that of Earth, the Venusian core is most likely at least partially liquid because the two planets have been cooling at about the same rate, although a completely solid core cannot be ruled out. The slightly smaller size of Venus means pressures are 24% lower in its deep interior than Earth’s. The predicted values for the moment of inertia based on planetary models suggest a core radius of 2,900–3,450 km.
Missions to Venus:
Many missions have been sent to Venus in the past decades. Venera 4 and 5, were the first to enter the atmosphere and send information. Venera 9 sent back the first images from Venus. Some other missions include- The Magellan Mission( a thirteen-year-long Venus radar mapping project ), The Pioneer Venus orbiters and Venus Express.
References: https://en.wikipedia.org/wiki/Venus#Atmosphere_and_climate https://en.wikipedia.org/wiki/Supercritical_fluid
Career counselling
Career counselling provide correct and consolidate information to our young brigade by giving them whole basket of available option after school is par excellence.The exposure to technology ,Media and Social Networking on a larger scale has made our youth aware to a great extent ,but they are little aware of the authenticity of information which are exposed to on a regular basis .ITS VERY IMPORTANT for our young and dynamic students to have proper and worthy information which is only possible through proper and useful career counselling.
Know asteroids better on World asteroid day
June 30 is the world asteroid day and it is held on the anniversary of Siberian Tunguska event which is known as one of the most dangerous asteroid related event on earth. This day is designed by United Nations general assembly to raise awareness about the harmful effects of asteroids and measures to be taken to avoid these effects. On this day lets know more about the asteroids.
After the formation of the solar system, some of the rocky remains which failed to form a planet started to revolve around the sun around 4.6 billion years ago and these are called asteroids. Asteroids are made of same starting materials as earth and the other planets. But they are not big enough to be called a planet. Currently 1,097,065 is the known asteroid count and there is an asteroid belt between Jupiter and Mars which contains more than 200 asteroids of size larger than 60 miles in diameter. And many asteroids are present outside the belt also.
asteroids can be very big of 940km and can be very small of 6-foot-wide. They are irregularly shaped although some are nearly spherical. Their surface is pitted as moon`s surface. Some of the asteroids also have their own moon. There are binary asteroids also present which revolve around the sun in pair and revolve around each other too. The average temperature on their surface is minus 73 degree Celsius.
THERE IS A CLASSIFICATION FOR ASTEROIDS BASED ON THEIR COMPOSITION

C-type asteroids: They are also called as carbonaceous asteroids. This is the most common type of the asteroid making 75% of the population. They are mostly grey in color. They have large amount of carbon with rocks and minerals. They inhabit the main belt`s outer region.
M-type asteroids: They are also called as metallic asteroids. They are mostly made of nickel and iron and small amount of stone. They are moderately bright and red in color. They are in the middle region of the main belt.
S-type asteroids: They are also called as siliceous asteroids. They are of 17% of the total asteroids present at inner region of the asteroid belt. They are mostly made of silicate materials. Their composition is similar to meteorites.
CAN ASTEROIDS BE A SPACE COLONY FOR HUMANITY?
The desperation of the humanity for survival is the main driving force to think about colonizing the asteroids. But this has many obstacles. The main challenge is the transportation. Asteroid belt is 204.43 million miles away from the earth & journey to them may take more than 18 months. And size of the asteroids is not enough to produce gravity. This makes landing on them difficult. Another problem is the temperature which is very less. Scientist are studying to remove all these obstacles and possibility of habiting on the asteroids is quite at the far end of the future.
MINING ON ASTEROIDS

Mineral depletion is becoming a major thing on the earth. It is predicted that earth will run out of the minerals in coming 50-60 years. So extraction of minerals from the space that too asteroids sounds interesting and hopeful. Asteroids also contain water which can be used as fuel for the spacecrafts used. Its been said that the world`s first trillionaire will be a person who owns asteroid mining. Asteroid mining will bring the essential economic progress.
Mining on asteroids requires a lot amount of resources. Some of may include mining robots and haulers. Construction and maintenance of infrastructure is important. In-space manufacturing should be enabled to do mining effectively. Bringing the mined materials back to earth is also a challenge.
The technology for asteroid mining is being constructed by a company called Deep space industries. They are developing 3 types of spacecrafts. They are: Fireflies to examine the asteroids, Dragonflies to bring back samples to the earth and Harvesters to voyage to the asteroids and gather tons of minerals and return back to the earth. TransAstra is another company which is developing technologies for the same. If all these companies succeed then the dream of mining on asteroids will come true and will benefit the earth`s economy.
Randomised Controlled Trial
The 2019 Nobel Prize in Economic Sciences was awarded to Abhijit Banerjee and Esther Duflo, who currently work at the Massachusetts Institute of Technology, and Michael Kremer of Harvard University. The Prize committee noted that these economists “introduced a new approach to obtaining reliable answers about the best ways to fight global poverty.” The new Nobel laureates are considered to be instrumental in using randomised controlled trials to test the effectiveness of various policy interventions to alleviate poverty.
So what is randomised control trial?
A randomised controlled trial is an experiment that is designed to isolate the influence that a certain intervention or variable has on an outcome or event. A social science researcher who wants to find the effect that employing more teachers in schools has on children’s learning outcomes, for instance, can conduct a randomised controlled trial to find the answer. The use of randomised controlled trials as a research tool was largely limited to fields such as biomedical sciences where the effectiveness of various drugs was gauged using this technique. Mr. Banerjee, Ms. Duflo and Mr. Kremer, however, applied RCT to the field of economics beginning in the 1990s. Mr. Kremer first used the technique to study the impact that free meals and books had on learning in Kenyan schools. Mr. Banerjee and Ms. Duflo later conducted similar experiments in India.
Why is randomised controlled trial so popular?
At any point in time, there are multiple factors that work in tandem to influence various social events. RCTs allow economists and other social science researchers to isolate the individual impact that a certain factor alone has on the overall event. For instance, to measure the impact that hiring more teachers can have on children’s learning, researchers must control for the effect that other factors such as intelligence, nutrition, climate, economic and social status etc., which may also influence learning outcomes to various degrees, have on the final event.Randomised controlled trials promise to overcome this problem through the use of randomly picked samples. Using these random samples researchers can then conduct experiments by carefully varying appropriate variables to find out the impact of these individual variables on the final event.
What are some criticisms of randomised controlled trials?
A popular critic of randomised controlled trials is economist Angus Deaton, who won the economics Nobel Prize in 2015. Mr. Deaton has contended in his works, including a paper titled “Understanding and misunderstanding randomised control trials” that simply choosing samples for an RCT experiment in a random manner does not really make these samples identical in their many characteristics.
While two randomly chosen samples might turn out to be similar in some cases, he argued, there are greater chances that most samples are not really similar to each other. Other economists have also contended that randomised controlled trials are more suited for research in the physical sciences where it may be easier to carry out controlled experiments. They argue that social science research, including research in the field of development economics, may be inherently unsuited for such controlled research since it may be humanly impossible to control for multiple factors that may influence social events.







You must be logged in to post a comment.